Read on:
VMware for Beginners – What is vSphere Distributed Switch: Part 15(a)
In this vSphere Distributed Switch part (b), we will continue to discuss this subject and focus on the vDS features.
What will we discuss in this second blog post about vSphere Distributed Switch?
- vSphere Distributed Switch Features
- vSphere Distributed Switch requirements
vSphere Distributed Switch Features (part two)
I’ll continue explaining each feature in detail of the vSphere Distributed Switches. Next, we will discuss Port binding & Port allocation.
Port binding & Port allocation
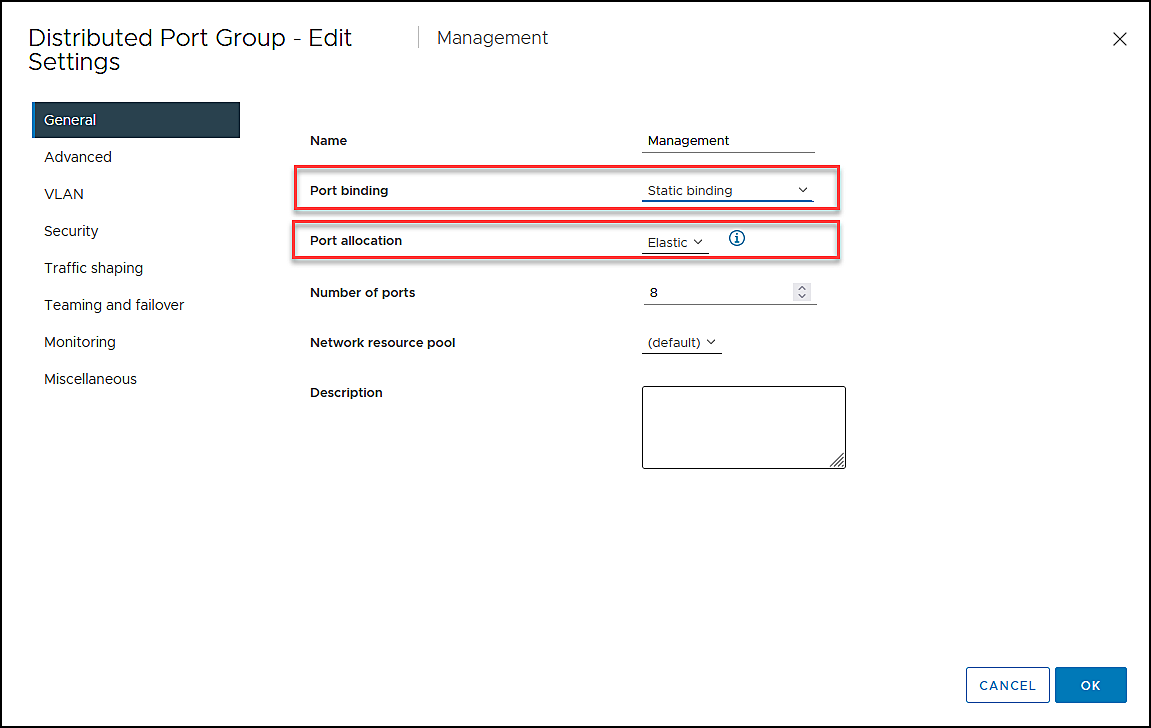
Here is a quick explanation of Port Binding:
- Static binding
Connects a virtual machine to a distributed port group by assigning a distributed port. - Ephemeral binding
The behavior is similar to a standard virtual switch (VSS) when you choose this choice. In the port group, one port is allocated for each connected virtual machine up to the maximum number of ports available. The number of ports is automatically set to 0, and each port group is allocated one port.Note: This option is very useful for connecting vCenter Appliance. If vCenter goes down, we still have a network since Ephemeral Is not bound to vCenter.
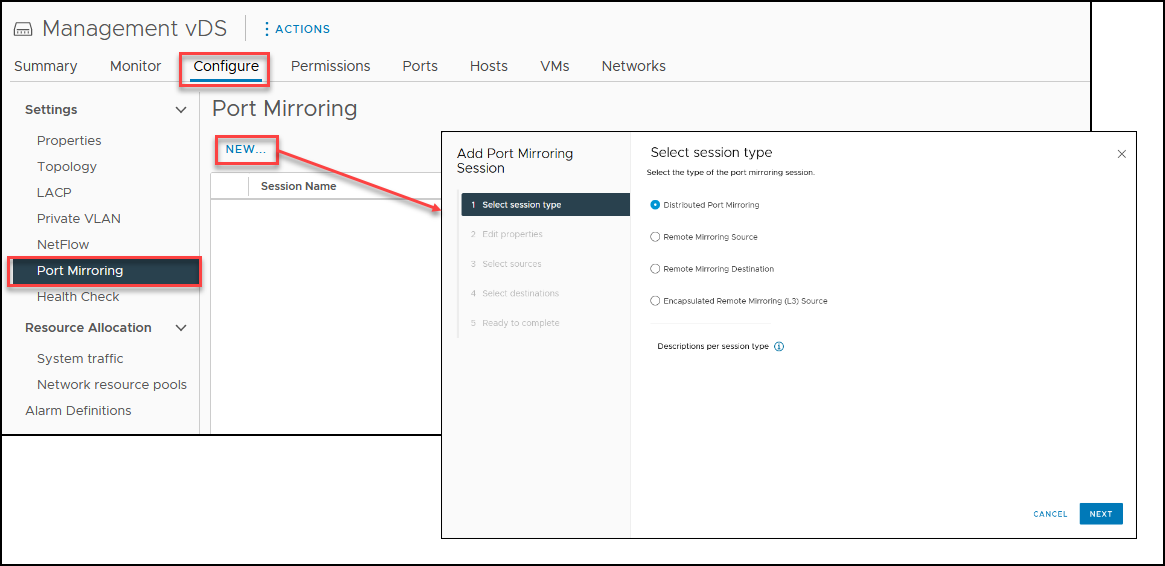
Port Mirror
Port Mirror is mainly used for traffic analyses and troubleshooting. It could be used to analyze packet drops or security.
In a vSphere Distributed Switch (vDS), Port Mirroring is a feature used to copy network traffic from a source port or set of ports to a destination port, which can be monitored or analyzed for troubleshooting, security, or other purposes.
With Port Mirroring, administrators can create a copy of the network traffic passing through a virtual switch and direct it to a destination port or virtual machine, where it can be captured and analyzed using a network analyzer such as Wireshark. This allows them to gain insight into the network behavior, detect security threats or troubleshoot issues.
To configure Port Mirroring in vDS, administrators must first create a port mirror session by defining a source port or set of ports and a destination port or virtual machine. They can specify the direction of traffic to be copied, either ingress (incoming traffic) or egress (outgoing traffic), or both. The administrator can also limit the amount of mirrored traffic by setting a filter based on protocols, VLANs, or MAC addresses.
Once the port mirror session is configured, the selected traffic will be copied to the destination port or virtual machine, which can then capture and analyze the data. It is important to note that Port Mirroring can consume significant network resources and may impact the performance of virtual machines, so it is recommended to use it selectively and with care.
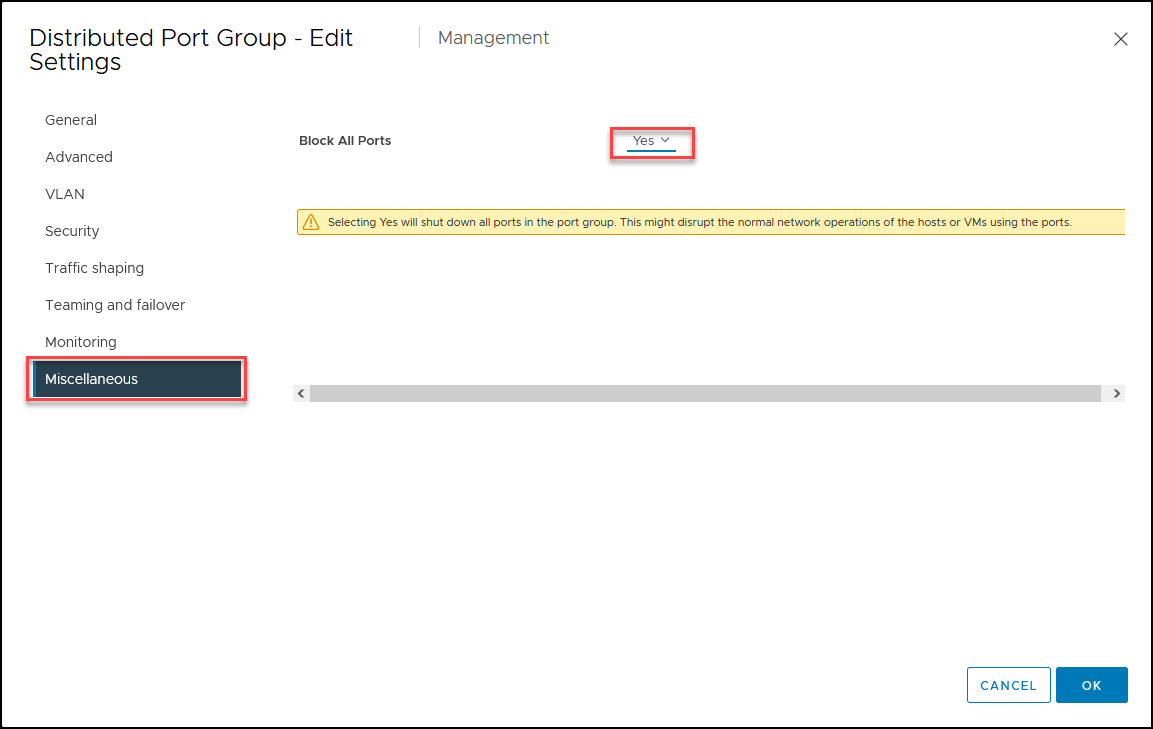
VM Port blocking
As the name identifies, VM Port blocking is a security feature to block traffic in a VM port.
In a vSphere Distributed Switch (vDS), VM Port Blocking is a security feature that allows administrators to restrict the network traffic that is allowed to enter or exit a specific virtual machine.
With VM port blocking, administrators can control the network traffic flow between virtual machines or between a virtual machine and the external network. This feature can be used to enforce network security policies, prevent unauthorized access, or protect sensitive data.
Once the rules are applied, any traffic that matches them will be blocked at the virtual machine’s port, preventing it from entering or exiting it. The administrator can also choose to log the blocked traffic, which can help in troubleshooting or auditing.
It is important to note that VM Port Blocking is only effective within the virtual environment and does not provide protection against attacks from outside the virtual infrastructure, so it should be used as part of a comprehensive security strategy only in a Virtual Machines perspective.
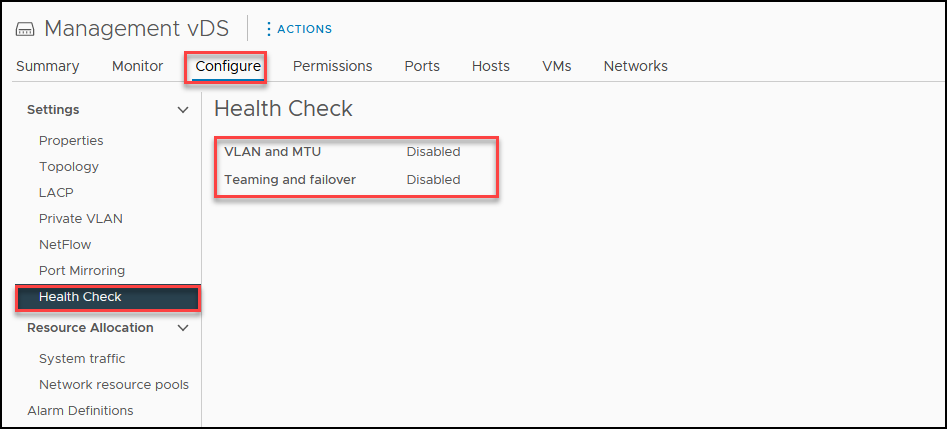
- Health Check (disable by default)VLAN and MTU
- Teaming and failover
Both Health Check features checks the traffic in the vDS and inform if any configurations are not correctly configured.
For example, if you set Jumbo Frames(MTU 9000), all the network devices connected to these ports must be enabled with Jumbo Frames.
If Jumbo Frames are not enabled on all devices, it can lead to packet fragmentation. This means that when a device tries to transmit a packet that exceeds the network’s maximum packet size, it has to divide the packet into smaller segments. These segments must then be reassembled at the receiving end, which can increase latency and reduce throughput.
Network resource pools
Network Resource Pools allow administrators to allocate a portion of the available network resources to a specific group of virtual machines. This can be useful in environments where some virtual machines require higher levels of network performance than others or where network resources must be reserved for critical applications.
When a virtual machine is powered on, it is assigned to a specific port group associated with a network resource pool. The virtual machine can then utilize the portion of the reserved network resources allocated to the pool it belongs to. This ensures that the virtual machine always has access to the bandwidth reserved for its pool, even during periods of high network congestion.
If we look at our infrastructure design, we see that we have Virtual Machines, for example, from Production and Development. Virtual Machines from Development should not have priority or use a big part of the bandwidth, so we create a Network Pool where they can only use the bandwidth allocated to them and provide Production VMs more bandwidth.
In this case, we use a Network resource Pool to prevent development VMs from monopolizing network resources and degrading overall network performance.
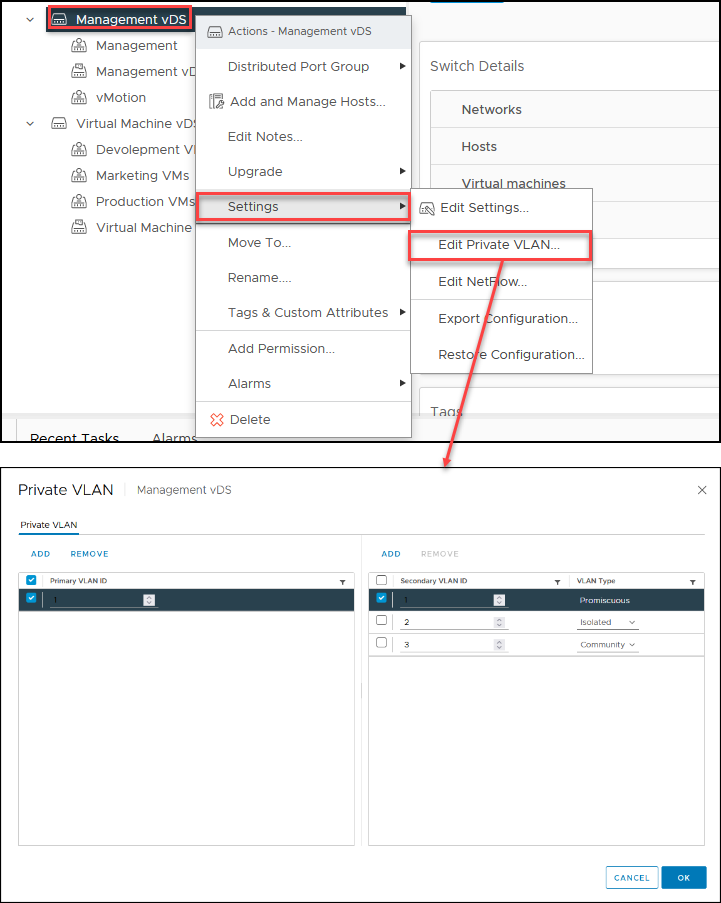
Private VLANsPVLAN Types: There are three types of PVLANs; Isolated, Community, and Promiscuous. Each type provides a different level of isolation and connectivity between virtual machines
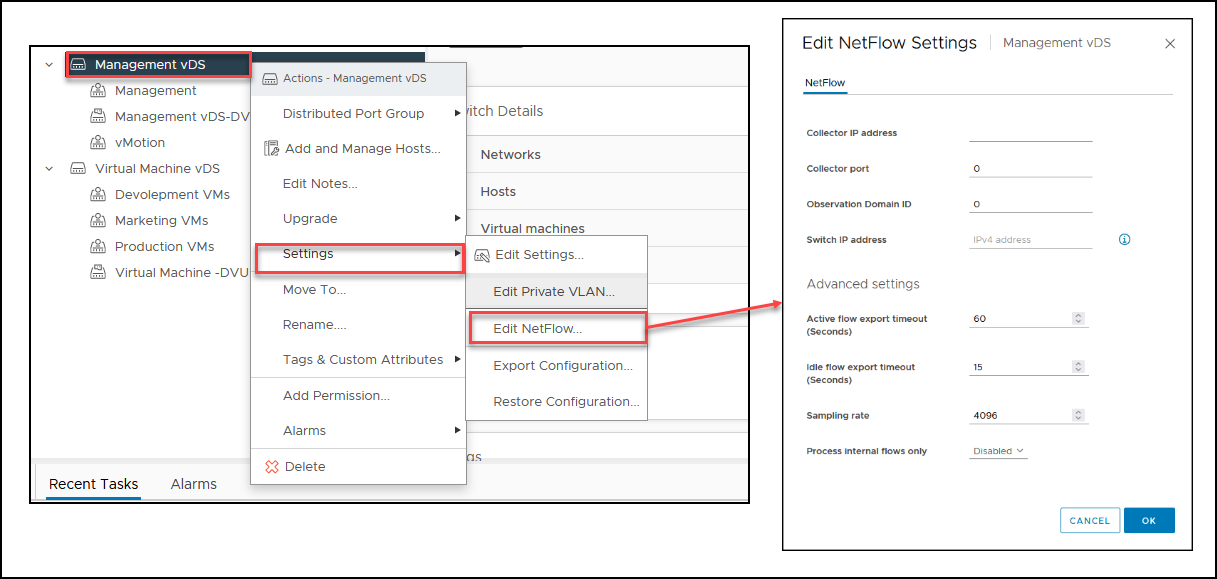
NetFlow
NetFlow collects information about each packet that enters or exits a virtual machine’s network interface, including the source and destination IP addresses, protocols, ports, and other metadata. This information is then aggregated and sent to a NetFlow collector, which can be used to analyze the network traffic patterns and identify potential issues.
Once NetFlow is enabled, the vDS will start collecting information about the network traffic flow and sending it to the designated NetFlow collector. The collected data can be used to generate reports, troubleshoot network issues, monitor network performance, and detect security threats.
By using NetFlow in vDS, administrators can gain visibility into the network traffic flow, identify potential bottlenecks, and optimize network performance. It can also help identify network security threats and provide insights into virtual machines’ network behavior.
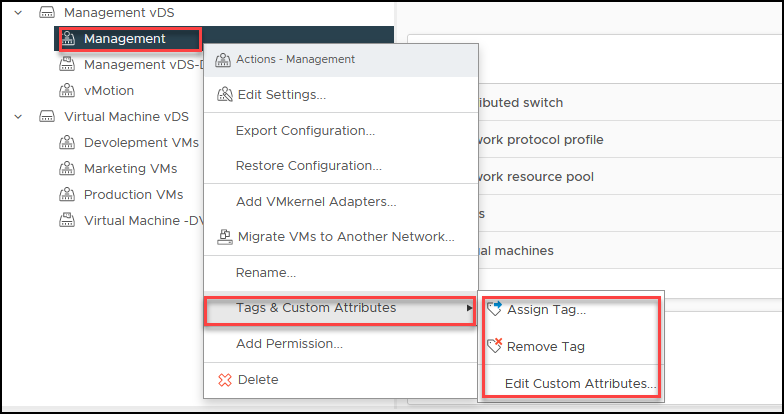
vDS Tags and Custom Attributes
Both Tags and Custom Attributes in vDS can perform bulk operations, such as filtering, sorting, searching, and reporting, which can help manage large-scale virtual environments. For example, administrators can use Tags to apply security policies or configure Quality of Service (QoS) settings across groups of virtual machines.
Custom Attributes can be used to track compliance requirements, maintenance schedules, or licensing information for virtual machines.
vSphere Distributed Switch requirements
Although the prerequisites for using vSphere Distributed Switch are not extensive, specific requirements must be fulfilled. These include:
- License: vSphere Distributed Switch is only available if you have a vSphere Enterprise Plus license for your ESXi hosts. This license provides access to advanced vSphere features, including distributed switching.
- vCenter Server: vSphere Distributed Switch is only available in vCenter. So you must be running vCenter Server to create a vSphere Distributed Switch. You cannot use vSphere Distributed Switch if you are running standalone hosts not connected to vCenter Server.
- Hardware Requirements: There are not many hardware requirements to use vDS, but the ESXi host needs at least one physical Ethernet adapter per host to configure and use a vDS.
- VLANs: If you are using VLANs with vSphere Distributed Switch, you need to ensure that the VLAN IDs are consistent across all hosts that are connected to the Switch.
With vSphere Distributed Switch requirements, we finish this second blog post about vSphere Distributed Switch.
In the next blog posts in VMware for Beginners series, we will discuss how to create and configure the vSphere Distributed Switch.
Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.

