One of the most important aspects of storing data in the cloud is not just the actual storing of the data, but protecting the data from attack, loss, and other threats. Microsoft Azure storage firewalls and virtual networks provide many great features to help protect your Azure storage accounts. In this AZ-104 study guide, let’s look at how to configure Azure Storage firewalls and virtual networks in the Azure portal for a layered security model.
What is the Azure Storage Firewall?
The Azure Storage firewall helps to provide a layered security model for your Azure storage. Azure storage firewalls control access through public endpoints, so you can configure network rules, so that only the applications requesting data from allowed networks can reach the data successfully.
You can limit requests based on the following:
- IP addresses
- IP address ranges
- IP subnets
You can apply storage firewall rules to existing storage accounts or when you create new storage accounts.
What role do virtual networks play in Azure storage
Virtual networks in Azure create an isolated environment, where you can securely operate your storage accounts. Storage account integration with virtual networks allows for forming a secure network boundary to increase the security of your data.
It helps to protect your storage accounts from unauthorized access and makes sure the traffic to and from your storage accounts is routed securely.
Default network access rule and changing this configuration
The Azure storage accounts have a default network rule configuration out of the box. These rules define the network access parameters, allowing you to specify which IP addresses, IP ranges, or virtual network subnets can access your storage account. By default, the storage accounts accept connections from any network, including any source IP, etc.
You can see this is the case if you pull up the default Security + network blade for your Azure storage account.
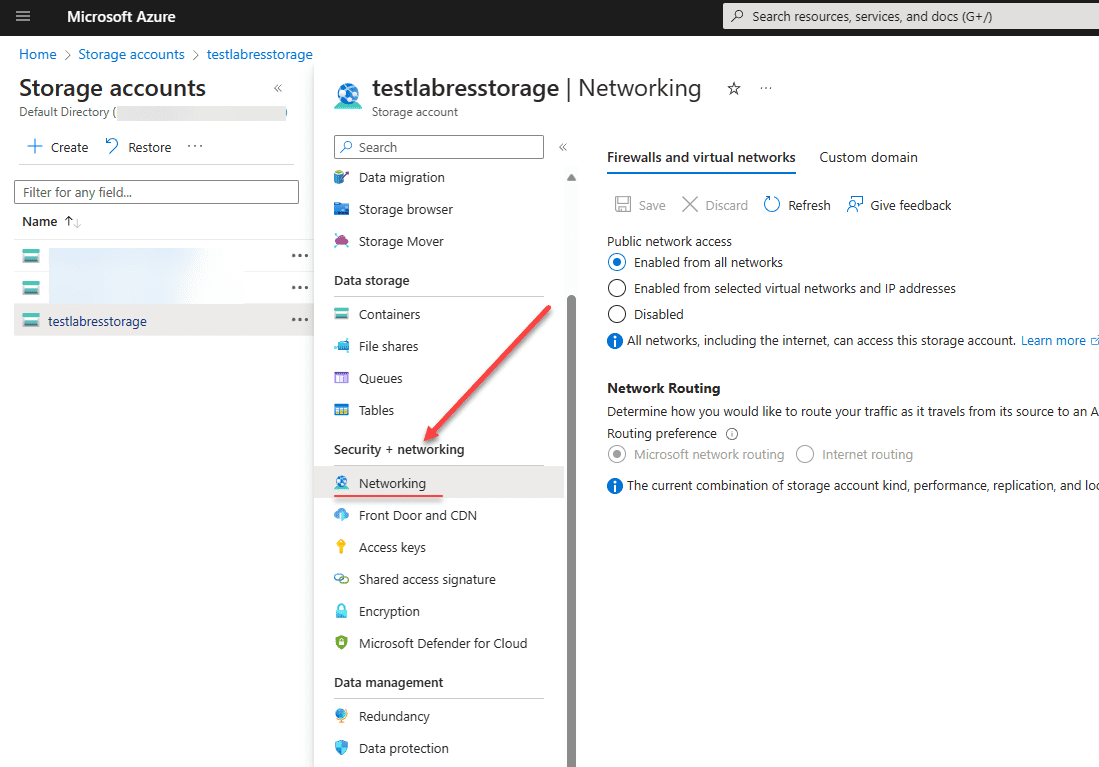
Changing Storage Account Firewall Settings
With the storage account firewall settings, you can define specific network rules, including service endpoints and virtual network rules, to allow or deny traffic to your storage accounts. Configuring these settings helps enforce that only trusted connections are permitted to access data in the Azure storage account.
Permissions needed
To make changes to the virtual network or virtual network firewall rules, you need to have the following permissions:
- The Storage Account Contributor role
- User with these permissions Microsoft.Network/virtualNetworks/subnets/joinViaServiceEndpoint/action
As a note, these permissions can be granted for someone in a different subscription, but can only be done using the Azure CLI, PowerShell, or REST APIs. You can view these permissions from other subscriptions using the Azure Portal but not make changes or add them there.
Service Endpoints and Private Endpoints in Azure
Service endpoints and private endpoints play an important role in Azure network security. Service endpoints provide secure pathways from your virtual networks to Azure services. Private endpoints create a direct, private connection to Azure services. These endpoints ensure that your network communications remain secure and isolated from public internet traffic.
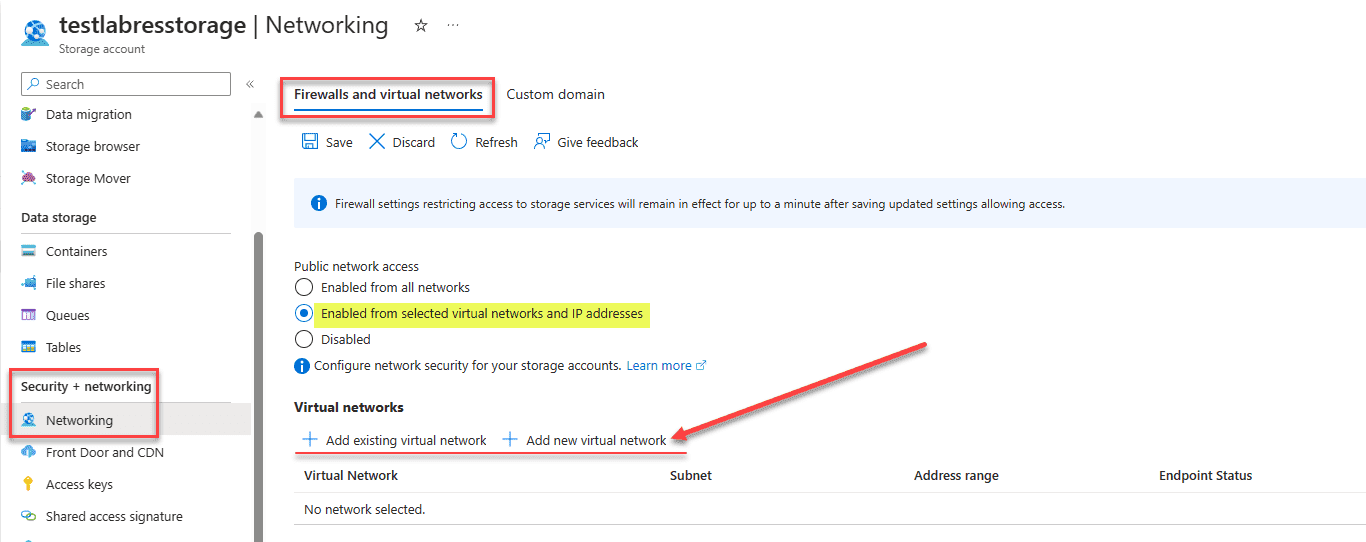
Enabled from selected virtual networks and IP addresses
You can enable a service endpoint for Azure Storage within the virtual network. The service endpoint is used for more efficient routing. You can route traffic from the virtual network down the best path to the Azure Storage service.
Under the Public network access section, select the radio button Enabled from selected virtual networks and IP addresses.
When you do that, you will see the options available to + Add existing virtual network and + Add new virtual network.
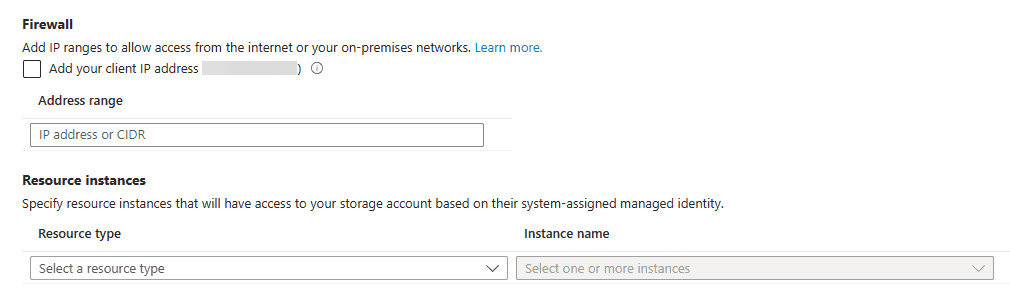
Next, we have the Firewall and Resource instances configuration. Under the firewall section, you can Add IP ranges to allow access from the Internet or your on-premises networks.
Resource instances allow you to specify resource instances that will have access to your storage account based on their system-assigned managed identity. This includes setting up rules for public IP address ranges and private IP addresses.
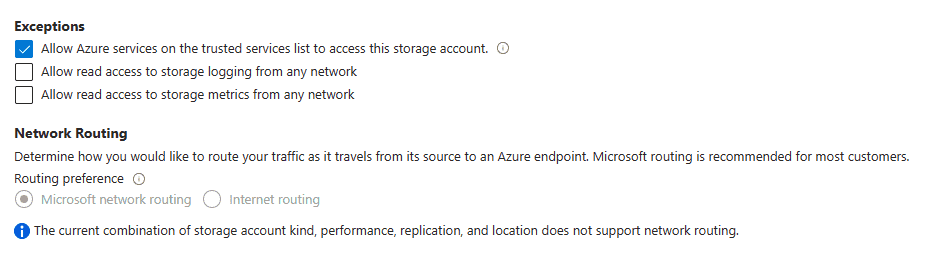
Finally under the Exceptions section, you have three options here:
- Allow Azure services on the trusted services list to access this storage account.
- Allow read access to storage logging from any network
- Allow read access to storage metrics from any network
Under the Network Routing section, you can choose how you want your Azure Storage traffic routed from the source to the destination Azure endpoint. By default, this is set to Microsoft network routing and is the recommendation from Microsoft, as opposed to Internet routing.
This option will be greyed out based on the storage account type, performance, replication, and location, among other factors.
Things to keep in mind
You will need to remember a few things about the Azure storage firewall and virtual network. Note the following:
- You can’t use IP network rules to restrict clients in the same Azure region as the storage account from accessing data
- Likewise, you can’t restrict access to services in the same region as the storage account from accessing it
- You can restrict access for clients in a paired region
These limitations must be noted when architecting and designing Azure storage account access for clients and services.
Wrapping up
Microsoft Azure storage firewalls and virtual networks are a great tool for the Azure administrator to use to ensure only clients and services from allowed networks are able to connect. You can use the IP rules and IP ranges as well as routing options to control traffic to the storage account. Keep in mind the caveats of clients or services in the same Azure region as it limits the ability of the IP rules to filter traffic.
Read More:
Microsoft Azure Administrator: AZ-104: Mastering Azure Storage Explorer – Part 21
Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.



Leave A Comment