One of the concepts to be familiar with in the AZ-104 exam is the management of Guest accounts. Guest accounts provide enhanced collaboration and security features for working with third parties with external accounts who may not natively have Microsoft Entra ID accounts (formerly Azure Active Directory). Let’s learn how to configure a Guest account in Entra ID.
What are Guest users?
Guest users, often called external users, are vital for businesses collaborating with partners, contractors, or other third-party associates who use external identity providers. With Microsoft Entra B2B collaboration and B2B users, organizations can seamlessly integrate external users or users into their workflows.
A Guest user account allows external identity provider individuals to access specific resources within an organization’s Microsoft Entra ID without being full members. This way, businesses can securely share resources with those outside the organization while maintaining control and data integrity.
The Guest account construct doesn’t require adding a Microsoft work or personal account to an existing Microsoft Entra ID tenant. Also, one of the great things about Guest users in Microsoft Entra ID, you don’t have to configure anything special to use Microsoft Entra B2B and external collaboration settings. They are on by default.
Apps, Groups, and Access Control
In Microsoft Entra ID, apps define a Guest user’s experience. By grouping apps and associating them with certain roles and assigning those roles to Guest user accounts, organizations can tailor the access resources provided to external collaborators. Admins can assign roles, manage access, and monitor activity through the Azure portal.
With the rise of enterprise applications, Microsoft Entra ID’s role is pivotal in ensuring that Guest users can interact with these apps effectively.
Example Guest use case
Imagine a scenario where a company, TechCompany Inc., collaborates with an external partner, NewCompanyDesign, on a software development project. TechCompany uses Microsoft Entra ID for their enterprise applications and resources. Instead of creating a permanent account for Mark, a lead designer from NewCompanyDesign, TechCompany chooses to add a Guest user account for him.
By using the “add Guest users” feature in the Microsoft Entra directory, they invite Mark using his Guest user’s email address. Once invited, Mark receives an invitation email with a direct link. He uses this link to access specific resources on TechCompany Microsoft Entra ID platform.
The integration ensures Mark can securely share resources and collaborate on the project, all while maintaining control and compliance from TechCompany end. Once the collaboration is completed, TechCompany can easily manage or restrict Guest user access for Mark, ensuring data security and integrity.
This Guest account method streamlines external collaboration without compromising security or functionality, making it an easy choice for access management for businesses looking to work with external partners or consultants.
Prerequisites for inviting Guest users
For adding Guest user accounts, note the following:
- You will need to log in as a user in the tenant directory, such as at least a Guest Inviter role or a User administrator, outside of the global administrator
- Access the Guest account email address to access the invitation
How to invite external users as Guest users
An admin, typically a global administrator, needs the Guest user’s email address to invite Guest users. The invitation process is started through the Microsoft Entra ID portal. Once the Guest user receives the invitation email, they can access the provided resources using a redemption link.
In the Microsoft Entra ID portal, the user’s external email address is configured as the user principal name in Microsoft Entra ID.
When you want to add Guest accounts to your Microsoft Entra ID (formerly Azure AD) tenant, the process is similar to adding internal users.
In the Users overview section, there’s an option to select + New user > Invite external user.
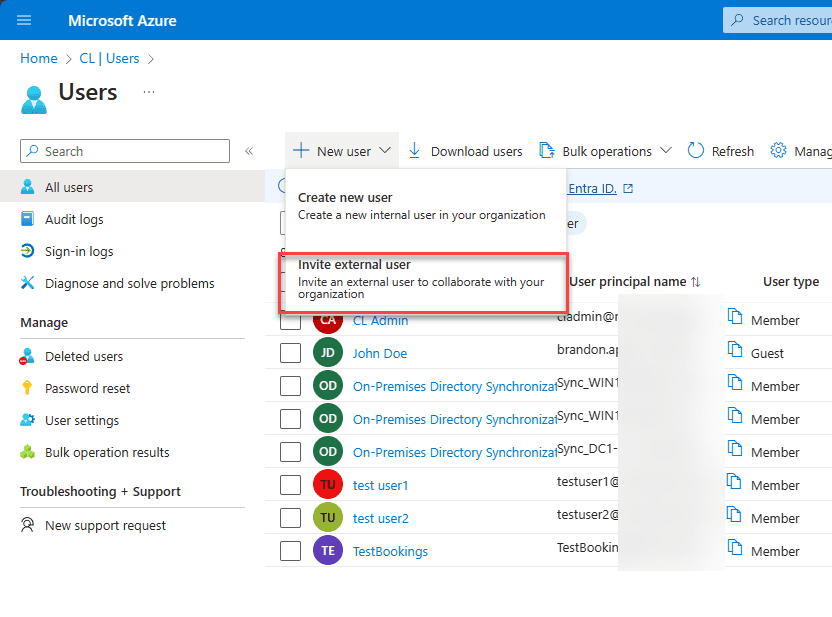
From here, input an email address along with a personalized message. This message, sent to the recipient’s email, contains a link for logging into your tenant. Clicking on “Invite user” not only adds the Guest to your Microsoft Entra ID tenant but also sends them the invitation:
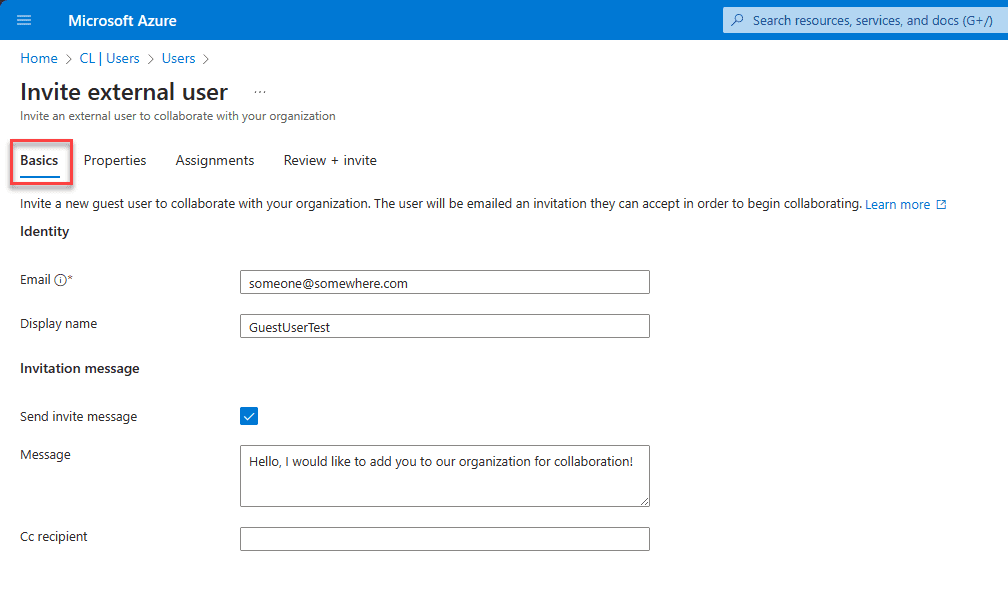
Clicking Next on the screen above will take you to the Properties screen, where you can fill in other details, including Identity information, Job Information, Contact Information, etc.
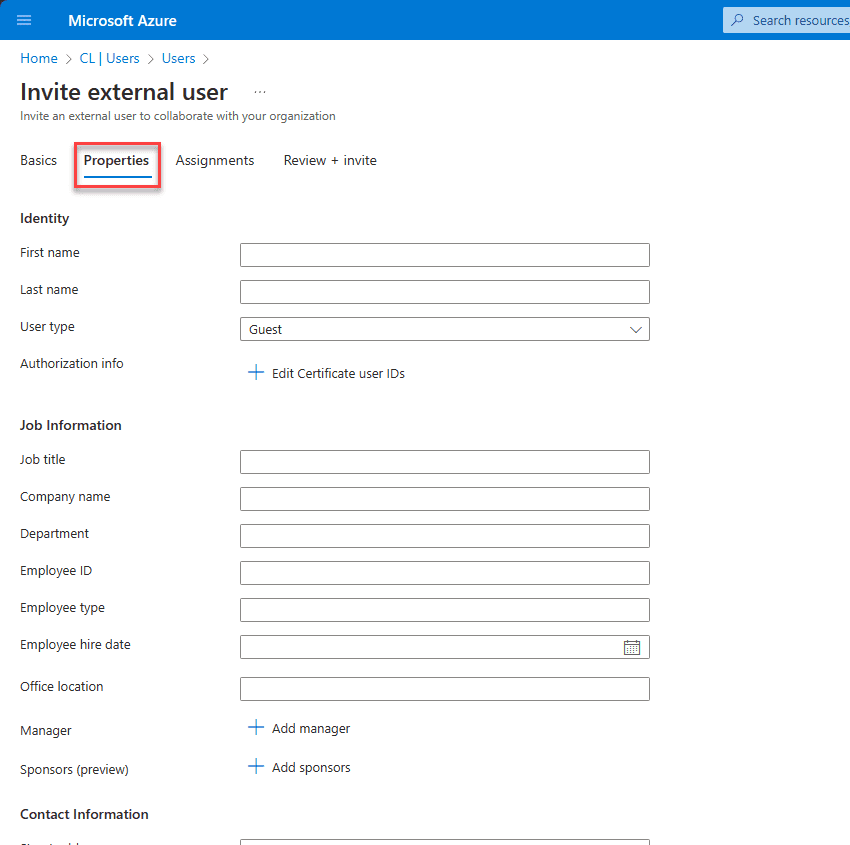
On the Assignments tab, you can add the user to a group or add a role during the invite process:
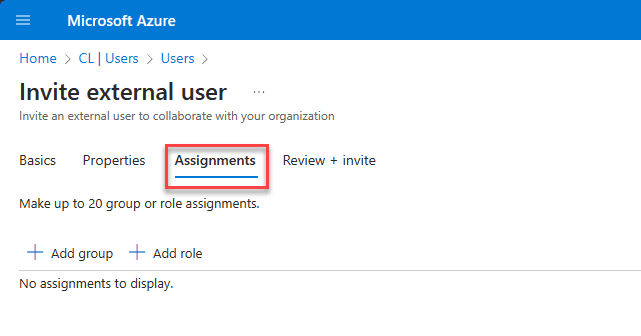
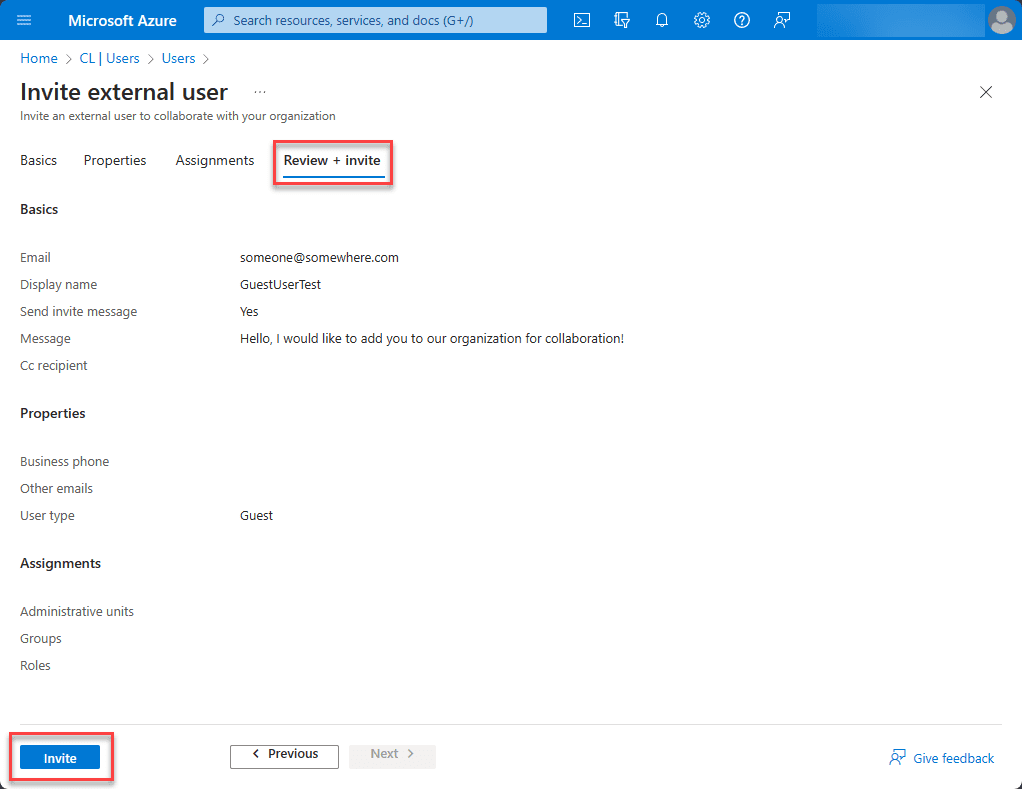
On the Review + invite screen, you can verify the information for accuracy and send the invite:
When the Guest user receives the invite, it will look similar to the following:

Managing external users after the invitation and acceptance is straightforward. You will find them in the Users overview section, where they are labeled as Guest under the User type category.

You can manage the user settings of your Guest user accounts by clicking on the Guest user account in the Overview section.
You can manage:
- Custom security attributes
- Assigned roles
- Administrative units
- Groups
- Applications
- Licenses
- Devices
- Azure role assignments
- Authentication methods
Conditional access
They can also apply security frameworks such as conditional access policies to such a user to extend the security protections of Entra ID to third parties.
You can create a conditional access policy for Guest user accounts with the following steps:
- Log into the Microsoft Entra admin center using an account with Conditional Access Administrator rights
- Navigate to Protection, followed by Conditional Access
- Click on “Create new policy.”
- Assign a descriptive name to your policy, ensuring it aligns with your organization’s naming standards
- In the Assignments section, opt for “Users” or “workload identities.”
- For the “Include” option, pick “All Guest and external users.”
- In the “Exclude” option, click on “Users and groups,” then select your organization’s emergency or break-glass accounts
- Navigate to “Target resources,” then “Cloud apps,” and for the “Include” section, choose “All cloud apps.”
- For the apps that don’t mandate multifactor authentication, use the “Exclude” option
- Move to “Access controls” and then “Grant.” Here, select “Grant access,” followed by “Require multifactor authentication,” and then hit “Select.”
- Review all your settings and switch the “Enable policy” to “Report-only.”
- Click “Create” to activate your policy
Self-Service Features and Guest Users
Microsoft accounts granted Guest access to your Microsoft Entra tenant, such as those from Hotmail.com, Outlook.com, or other personal email addresses, cannot use Microsoft Entra SSPR. You can find more details and specifics of these limitations here: Self-service password reset deep dive – Microsoft Entra | Microsoft Learn.
Wrapping up
By understanding the use of Guest user accounts, permissions, and app integrations, businesses can collaborate while maintaining the integrity and security of their data. Guest accounts show up in the Users section of Entra ID and provide the same workflow of management to managing native user accounts. You can also use conditional access and other tools to secure the environment further with Guest accounts.
Related Posts:
Microsoft Azure Administrator: AZ-104 : Bulk updates in Microsoft Entra ID – Part 4
Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.



Leave A Comment