One of the skills you will want to have a grasp on with the AZ-104 exam is managing device settings in Microsoft Entra ID. Let’s look at the settings and configurations you can manage for your devices associated with Microsoft Azure and where you configure these.
Understanding Microsoft Entra ID (Azure Active Directory)
To understand how you can control and manage devices in Microsoft Azure, we must first understand Microsoft Entra ID. Microsoft Entra ID (formerly Azure AD) is the core of Microsoft Azure’s identity management and device settings. It plays a central role in device registration, identity management, and conditional access.
Device Registration in Azure AD
Device registration is a crucial first step in managing devices within Azure. Azure AD Device Registration Service facilitates this process. The device registration service establishes a connection between devices and Azure AD, ensuring enhanced manageability and security features.
After the connection is established, the process to manage device settings from Azure is straightforward. There are various ways that devices can be “connected” with Microsoft Azure.
These include the following:
- AzureAdJoined – Joined to Azure Active Directory
- EnterpriseJoined – This type of join is joined to on-premises Device Registration Service (DRS) and can be referred to as “Workplace Join” (WPJ)
- DomainJoined – Joined to a legacy on-premises Active Directory Domain Services directory service
When devices are managed by Microsoft Entra, they can be restricted by what is known as conditional access policies. What are these?
Conditional Access Policies
Conditional Access in Azure AD is a powerful security tool that allows enforcing access policies based on various conditions like user roles, locations, and device states, ensuring secure access to resources.
Device settings along with conditional access policies
Device settings in Microsoft Entra is the foundation of device-based conditional access. Device-based conditional access can ensure your business-critical resoures and can only be accessed by managed devices.
Microsoft Entra ID Device Management
The process to manage device identities and device management is important for ensuring device compliance. Monitoring and auditing tools in Azure provide a solution for IT admins to maintain control over device settings and operations. You need to be a global administrator or a cloud device administrator to manage devices in Azure.
Managing Device Settings
Managing device settings in Azure involves many tasks, including configuring settings, managing device identities, and ensuring registered devices adhere to organizational policies. To get to your device management settings, in Microsoft Entra ID, navigate to Devices.
Next, click the Device settings link on the left-hand blade.
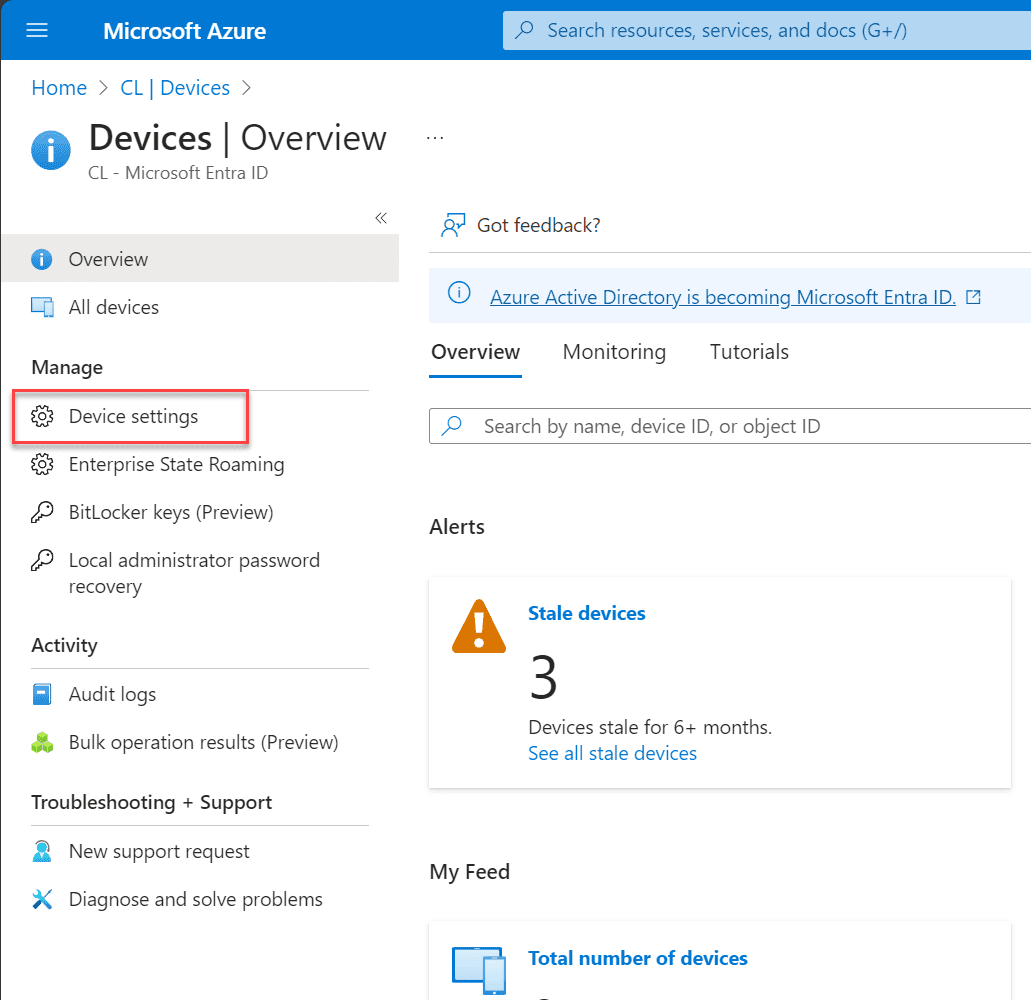
When you click the link, you will be taken to the device settings page that includes:
- Microsoft Entra join and registration settings
- Local administrator settings
- Other settings
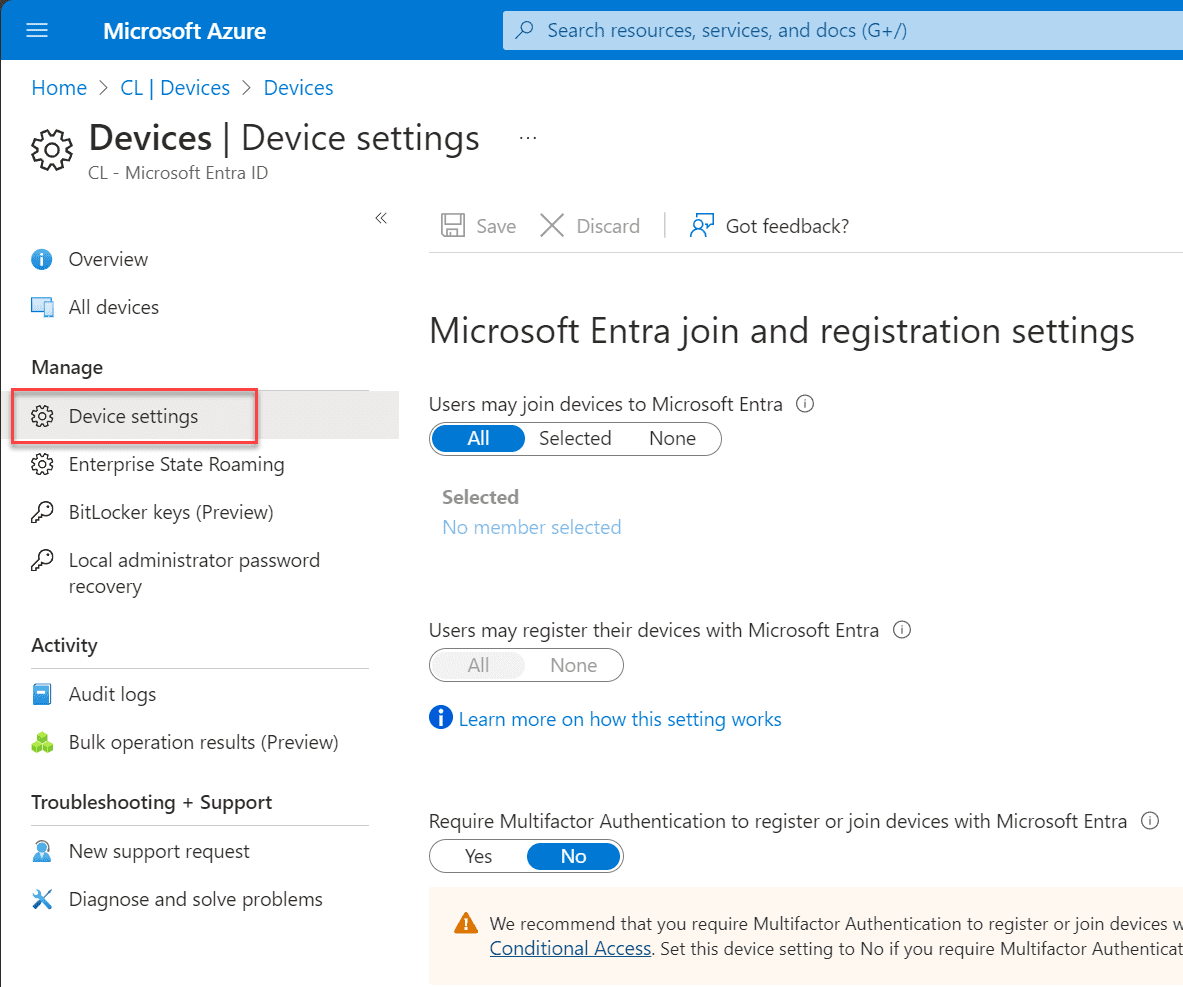
Notice the following settings that you can configure on this page:
Users may join devices to Azure AD: Under this setting, you can specify which users are permitted to join their devices to Azure AD. Note that this particular setting applies solely to Azure AD join on Windows 10 and 11.
Users may register their devices with Azure AD: Adjust this setting to permit device registration with Azure AD. You have two choices: None, meaning devices can’t register unless they are Azure AD joined or hybrid Azure AD joined, and All, allowing all devices to register. Registration is required for enrollment with Microsoft Intune or MDM for Office 365. If either service is configured, All is selected, making None unavailable.
Require Multi-Factor Authentication for device registration or joining with Azure AD: This option allows you to mandate Multi-Factor Authentication (MFA) during device registration. Before enabling this, ensure MFA is set up for users who will register their devices.
Maximum number of devices per user: Adjust this setting to define the maximum number of devices a user can register in Azure AD. The default is 50.
Manage Additional local administrators on all Azure AD joined devices: This setting enables the addition of extra local administrators for Azure AD joined devices.
Manage Enterprise State Roaming settings: This setting offers users a streamlined experience across their Windows devices, reducing the time to set up new devices.
Viewing your devices in Microsoft Entra ID
You can view the devices in your Microsoft Entra environment by clicking the All Devices menu option. Here you will see all the devices connected.
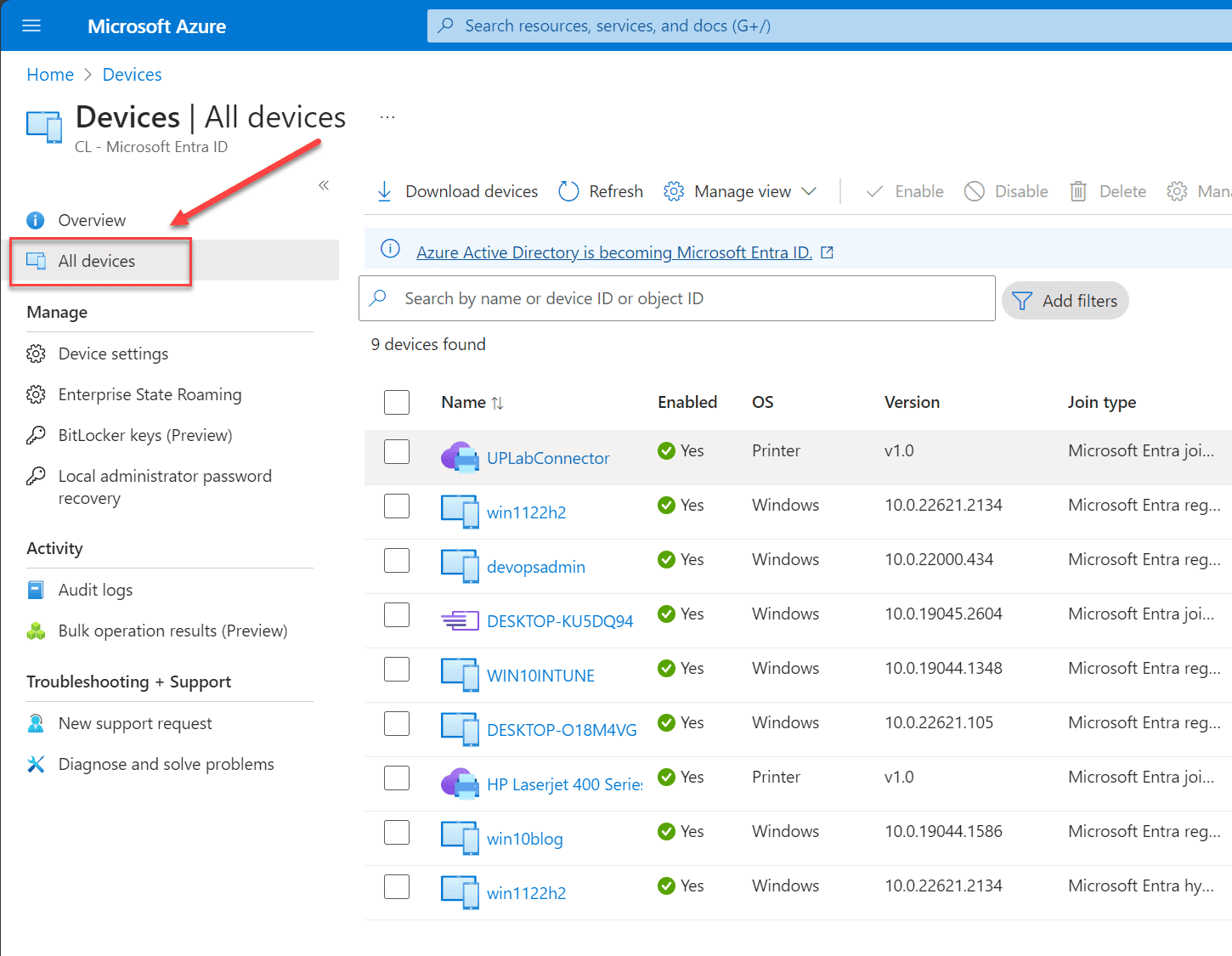
You can click any device to take you to the Properties page for the Microsoft Entra-registered device.
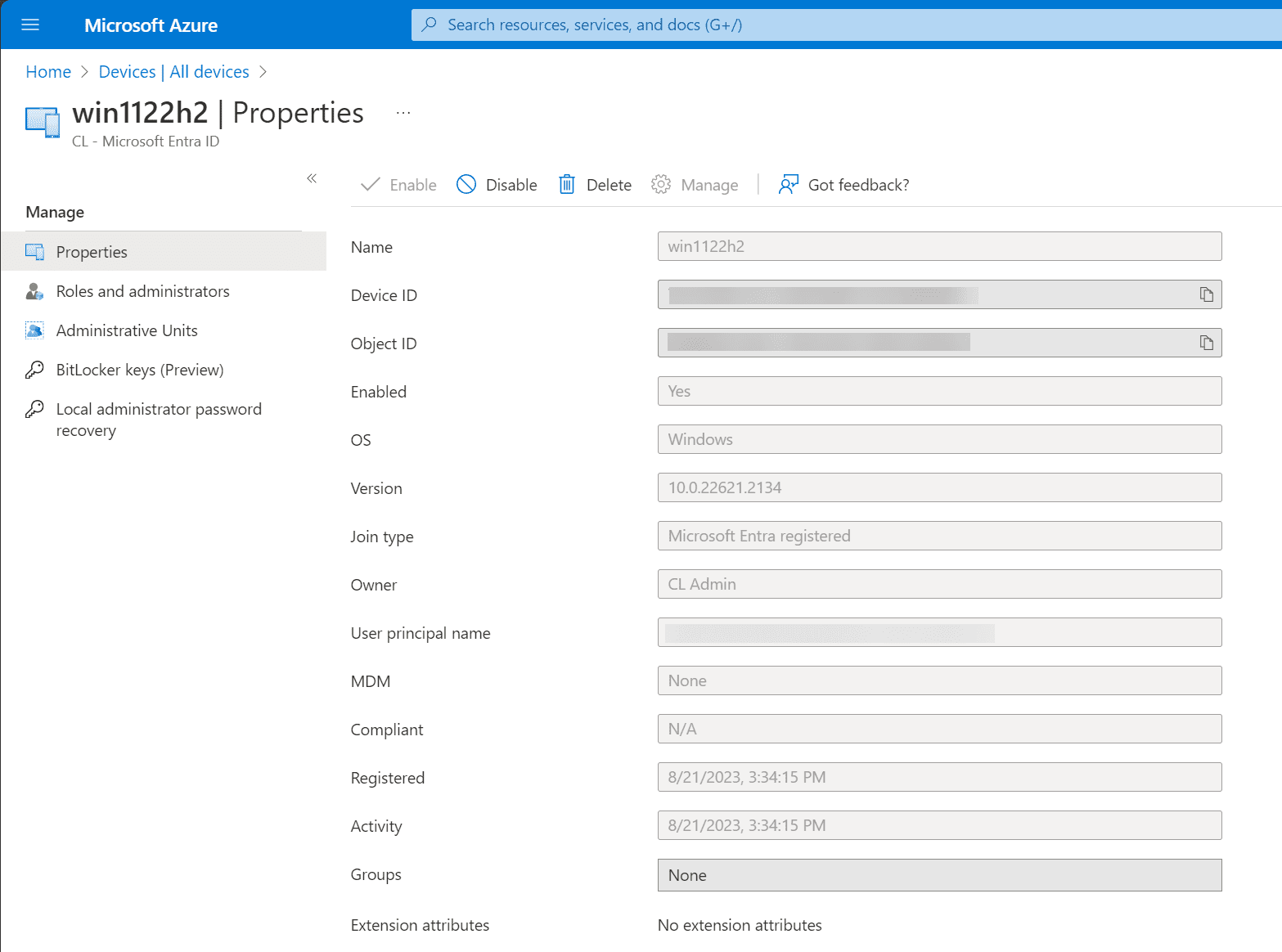
Device audit logs
You can view your device log history of events under the Activity > Audit logs menu. Here, you can view your logs and filter the logs for specific activities and devices.
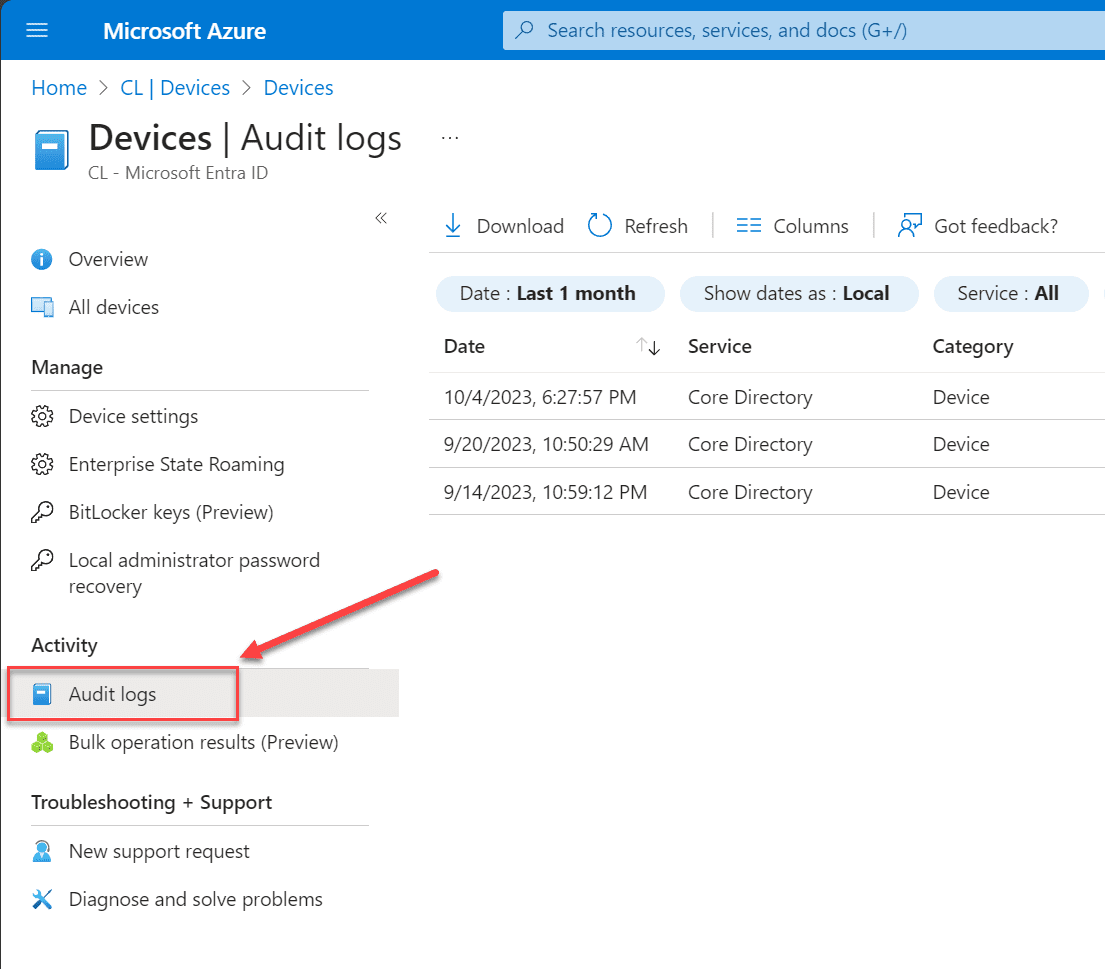
Microsoft Intune and Mobile Device Management
Microsoft Intune is a solution for comprehensive device management, extending beyond device settings management to broad device configurations and security protocols.
Azure’s Mobile Device Management (MDM) capabilities extend device management, ensuring a seamless experience managing various devices, including Windows 10, iOS, and Android.
Configuring Device Settings through Intune
Configuring device settings through Microsoft Intune streamlines device management and reinforces security by ensuring adherence to organizational policies.
Frequently Asked Questions
How does Azure AD device registration differ from Azure AD joining?
Azure AD registration is more about allowing devices to be known by Azure AD, enabling conditional access and other Azure AD-based features. On the other hand, Azure AD joining is a more comprehensive setup where a device becomes a full member of the Azure AD domain, allowing for additional control and settings management by the organization’s IT.
Can I manage both Windows and iOS devices in Azure?
Azure’s device management capabilities extend across various operating systems, including Windows, iOS, and Android. Through tools like Microsoft Intune, administrators can manage and configure device settings irrespective of the operating system.
What are the prerequisites for setting up Mobile Device Management (MDM) in Azure?
Before setting up MDM, ensure you have an Azure AD account and a mobile device management solution like Microsoft Intune. Having administrative privileges in Azure AD to configure MDM settings is also required.
How does Conditional Access bolster security in Azure AD?
Conditional Access in Azure AD enables enforcing access policies based on various conditions such as user roles, device state, and location. This ensures that access to resources is granted only under secure and compliant circumstances.
What roles do global administrators play in Azure device settings management?
Global administrators have the highest level of permissions and can configure any settings in Azure AD, including device settings. They can set up Conditional Access policies, manage user and device identities, and much more to ensure a secure and compliant environment.
Is Multi-Factor Authentication (MFA) necessary for device registration in Azure AD?
While MFA is not mandatory for device registration, it’s a highly recommended security practice. Requiring MFA during device registration adds an extra layer of security by verifying the user’s identity through multiple methods (factors) before granting access.
How does Microsoft Intune integrate with Azure AD for device management?
Microsoft Intune integrates seamlessly with Azure AD to provide a centralized platform for device management. This integration allows administrators to enforce compliance policies, configure device settings, and manage apps across all registered devices.
What is the significance of Enterprise State Roaming settings in Azure AD?
Enterprise State Roaming settings in Azure AD allow users to sync settings across Windows devices, simplifying the device setup process and ensuring a consistent user experience.
Wrapping up
Mastering the management of device settings is extremely important and is a topic you will want to be familiar with, in preparing for the AZ-104 exam. As we have seen, you can view and manage your devices from the Microsoft Entra dashboard, view audit logs, and configure and control who can register devices in Microsoft Entra ID, among other settings.
Related Posts: Microsoft Azure Administrator: AZ-104: Manage User and Group Properties: Part 2
Don’t miss out on the opportunity to enhance your data protection and recovery capabilities. Download and start your free trial today!
Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.



Leave A Comment