Every few days, new ransomware pops up. They have one thing in common: they encrypt files and make them unusable until the victim makes a payment to a non-traceable destination, mostly using Bitcoin or other cryptocurrencies. They target different types of data and various platforms. A few days ago, we talked about Rhysida ransomware, which targets Windows machines.
Today, we are discussing Abyss Locker, a new ransomware that, with the latest update version 2.0, targets the VMware ESXi virtualization environments and its virtual machines. We will explore Abyss Locker and its impact on VMware, as well as share tips on how to secure your VMware ESXi hosts.
Additionally, we will highlight how BDRsuite’s disaster and recovery technology can assist you in remaining composed, secure, and resilient against Abyss Locker’s attacks – proving that it can’t breach your defenses!
What is Abyss Locker
The first version of Abyss Locker was spotted in March, and the second version, designed specifically to target ESXi virtualization environments, was discovered a few days ago.
Abyss Locker operates as ransomware, encrypting VMware virtual machines (virtual disk, metadata, and snapshots) and demanding payment from victims in exchange for the decryption key.
Abyss Locker focuses on ESXi hosts with weak SSH credentials, using SSH brute force attacks as its means of entry. Once the attackers gain access to the ESXi host via SSH, Abyss Locker executes standard excli commands (listed below) to encrypt the virtual machines. After the virtual machines are encrypted, they are gracefully shut down, and the file extension is altered to include .crypt.
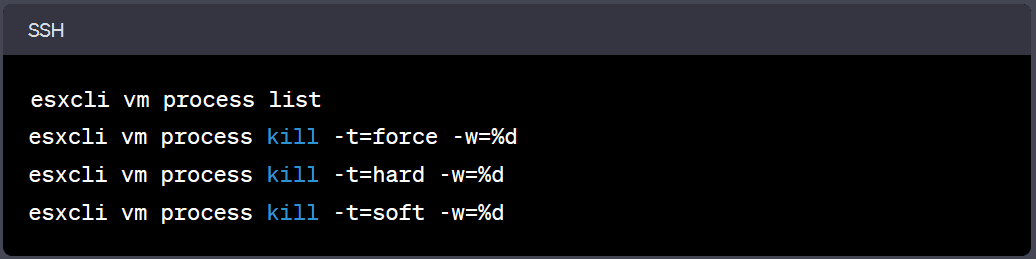
These commands are powerful and should be used with caution, especially when dealing with production virtual machines, as they may cause data loss or disrupt critical operations.
Once Abyss Locker encrypts the VMware data, it creates notes to instruct the victim on how to contact the attackers and make payment. They also instruct the victim not to waste time with authorities to solve the problem since only the attackers possess the decryption key and can provide help. Abyss Locker group claims that if the victim contacts the authorities, they will publicly expose the leaked data.
This is what the note looks like.
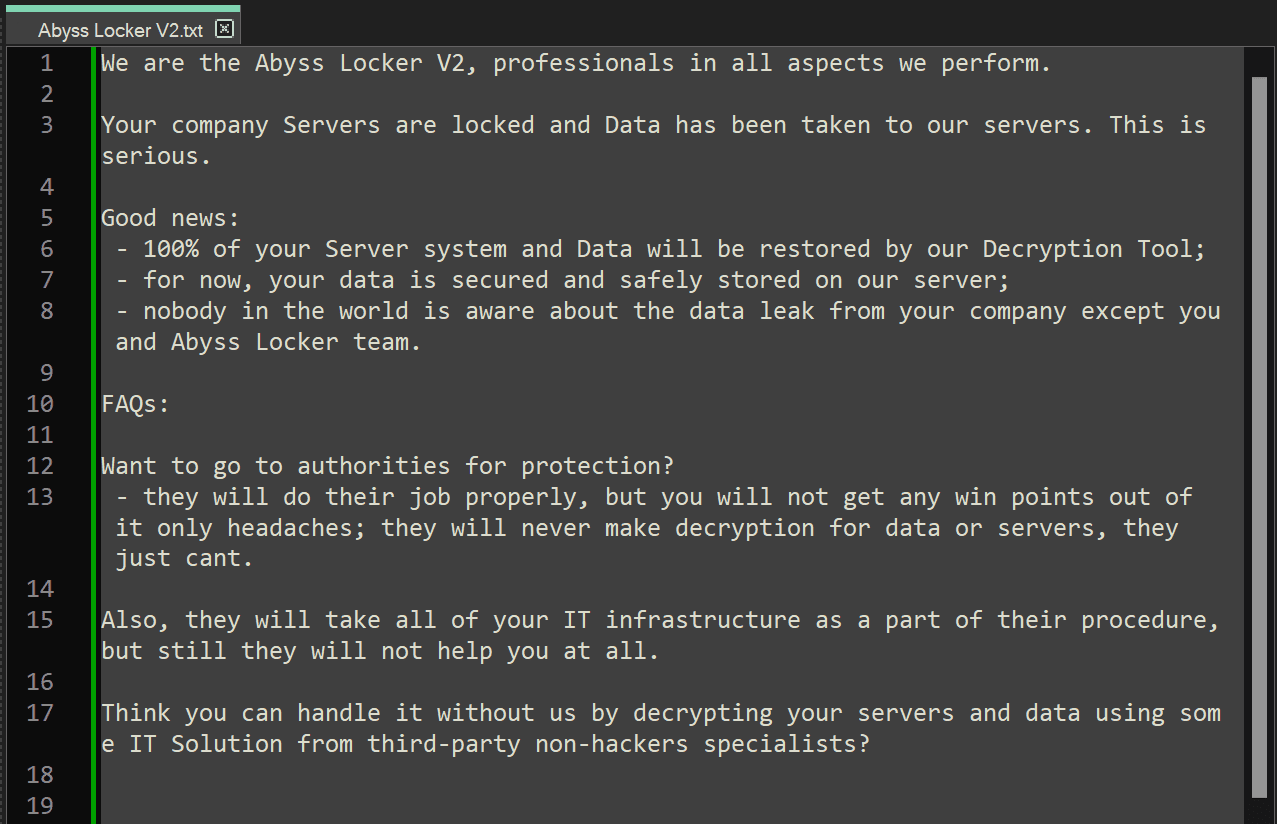
The general advice from cybersecurity experts and law enforcement agencies is not to pay ransomware attackers under any circumstances. Paying the ransom does not guarantee that the attackers will provide the decryption key, and it only encourages them to continue their malicious activities.
Instead, protect your VMware and implement a proper backup and recovery strategy. Would you like to learn how to do it? If so, please continue reading.
Wait, what is SSH?
There are two ways to access and manage your VMware ESXi: using the web interface and the command-line interface (CLI). SSH stands for Secure Shell and serves as the command-line interface for ESXi.
Harden your VMware ESXi
There are numerous practices available to secure your VMware ESXi, and VMware provides excellent documentation on the subject. However, in this section, we will concentrate on SSH since Abyss Locker exploits this entry point.
Before we start talking about SSH, there’s a general practice you should follow: keep your VMware ESXi virtualization environment up to date.
Keep your ESXi up to date
You should ensure that your underlying hardware, VMware ESXi, and vCenter are updated to the latest available versions. The underlying hardware refers to your physical server where you have installed VMware ESXi. For example, if you are running Dell PowerEdge, make sure to update the firmware, BIOS, RAID controller, iDRAC, Ethernet cards, and other components.
Security is a multi-layered approach that extends beyond just VMware ESXi.
Disable SSH
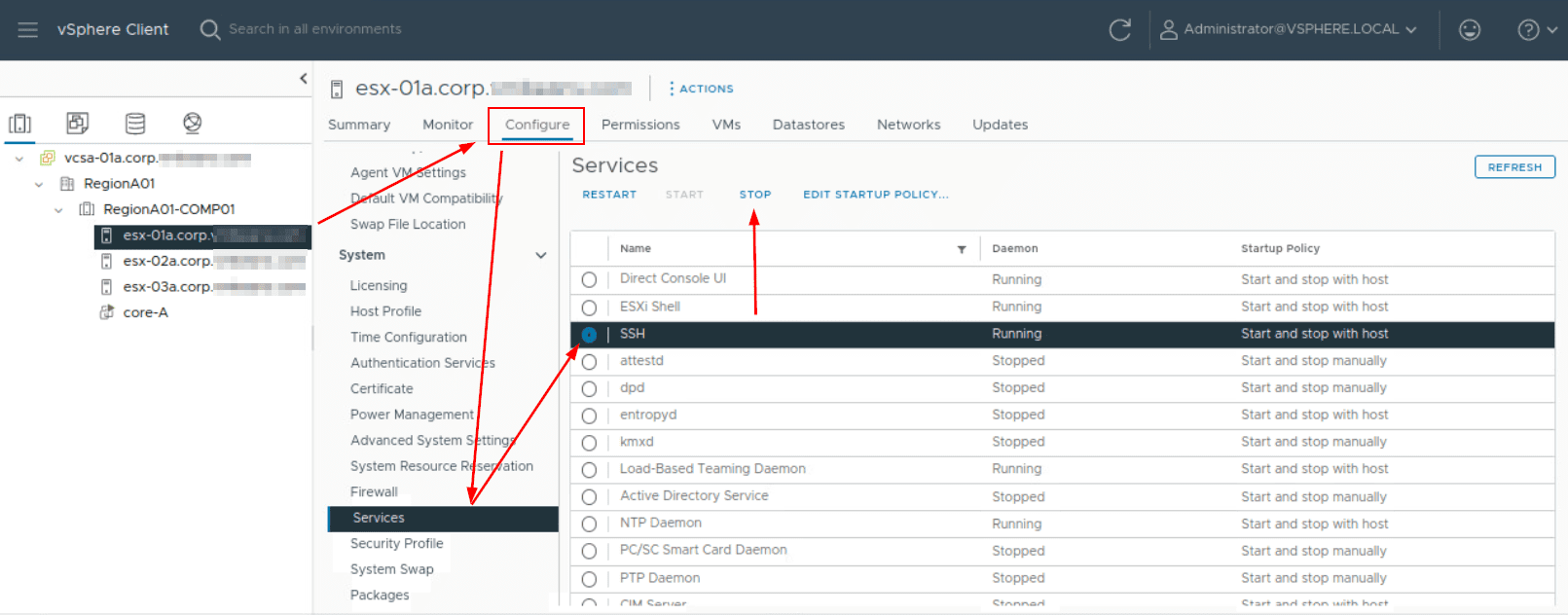
SSH is disabled by default. You can enable or disable it using the web interface. If you don’t use SSH and don’t need it, disable it. To do so, navigate to your ESXi host, go to Configure > Services, select SSH, and click ‘Stop’.
According to VMware, to reduce the risk of unauthorized access, activate SSH for troubleshooting only. For everyday activities, use the vSphere Client or vCenter.
You can increase the security of your ESXi by enabling ESXi Lockdown Mode. When enabled, all operations can only be performed via vCenter.
Additionally, your physical servers have a management interface (e.g. iDRAC for Dell, iLO for HP, iRMC for Fujitsu, IMM for IBM and Lenovo) that supports both Web and SSH access. If you don’t require SSH access to your physical server, it’s recommended to disable it.
If you prefer to have SSH enabled, here are some tips on how to harden its security.
Use SSH keys
SSH can be authenticated in two ways: using passwords and keys. Passwords are easy to set up and manage, but they are prone to brute-force attacks and phishing attempts. On the other hand, SSH keys are more secure but require more effort to set up and manage. SSH consists of two keys: a private key stored securely on the user’s local machine, and a public key uploaded to the remote server. SSH keys are considered more secure than passwords.
Change SSH port
SSH uses port 22, and many malicious malware are designed to check and attempt that port. By changing SSH to another port, you can minimize the risk and buy some time before your monitoring system informs you about unknown attempts.
Use a strong SSH password
When authenticating to SSH using a password, make sure to use strong passwords. Weak passwords can be easily hacked using brute force attacks. Ensure that your organization has strong password policies, such as a minimum of 10 characters, including both lowercase and uppercase letters, numbers, and special characters. It is also essential to regularly change your password (e.g., every 6 months).
This general rule should be implemented not only for SSH but also for any credentials within your organization. This is essentially how Abyss Locker gains access to VMware.
Set Idle Timeout
If you were using SSH to connect to your VMware, and finished your job, but forgot to sign out, you will remain signed in indefinitely, and this could be a potential risk exploited by an attacker. As a countermeasure, you should set an idle timeout to automatically log you off after X amount of seconds.
Set Availability Timeout
This is only valid in case you temporarily activate SSH when you want to use it. By configuring the availability timeout, you set the time that elapses before you must log in after SSH is activated. Once the timeout expires, and you don’t log in within the defined time period, the SSH service will be locked (stopped).
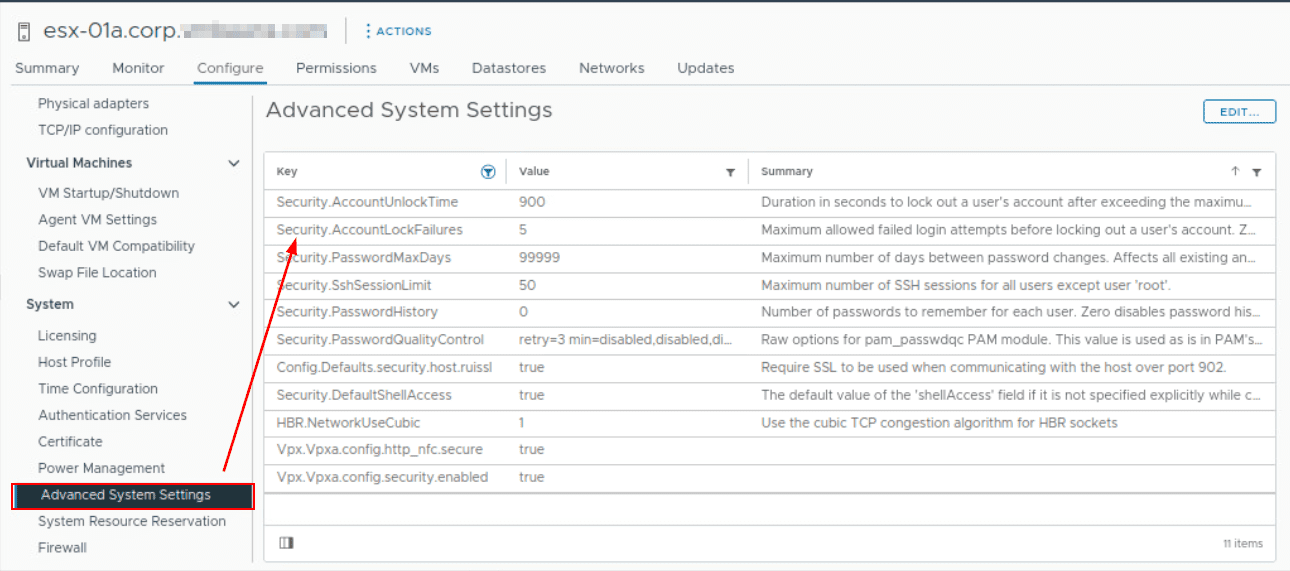
Enable ESXi Account Lockout
You can configure the system to lock a user after a certain number of failed attempts. By default, the user account will be locked for 15 minutes after five failed attempts. You can adjust this setting under the “System – Advanced System Setting“ of your ESXi host.
Disable root password
By default, VMware includes a user account called Root with all system privileges. It is highly recommended to disable this account and create separate user accounts that you will use to connect to ESXi via SSH. Also, ensure to employ the principle of least privilege, granting users only the necessary permissions for their respective tasks.
Enable Firewall Rules
You can configure firewall rules to allow SSH access only from trusted IP addresses or networks. When you limit the sources that can connect to your VMware, you mitigate the risk of unauthorized access.
Monitor SSH logs
Enable SSH logging and keep an eye on any SSH failed or successful attempts. You can enable SSH logging by navigating to ‘Advanced Settings’ in the vSphere Client, selecting the ‘Config.HostAgent.log.level’ option, and setting it to ‘info’.

Additionally, you can implement a SIEM (Security Information and Event Management) solution to automatically aggregate logs, analyze them, and trigger notifications in case of suspicious activities.
These were some of the tips you should consider to strengthen your SSH. In addition to SSH, ensure that your VMware ESXi virtualization environment is hardened from all different layers.
How BDRSuite can help you
Even after implementing all the mentioned security improvements, if Abyss Locker still finds its way into your VMware and encrypts your virtual machines, you can quickly get your workloads back online within minutes by using BDRSuite.
BDRSuite very soon supports immutable backups, which prevent any changes to the backed-up files. In practical terms, hypothetically speaking, if Abyss Locker were to get into VMware via SSH (we hope it will not) and encrypt files on the datastore, it will not be able to encrypt the backed-up files.
Even if your virtual machines are down, you can perform instant recovery in just a few minutes with BDRSuite.
BDRsuite supports VMware versions from 5.0 (although I hope you don’t run it) up to VMware 8.0. We regularly test BDRsuite to ensure compatibility with different ESXi versions.
If you didn’t know: BDRsuite is a comprehensive backup solution that has a lot to offer for your VMware ESXi environment. VMware can be integrated with BDRsuite in an agentless manner. Just a few clicks separate you from integrating VMware vSphere or vCenter with BDRSuite.
Once you integrate VMware with BDRsuite, you can select which virtual machines you want to backup and where to store the backups. You can follow the 3-2-1 backup policy, which means having three copies of your data, stored on two different media, with one copy offsite in either on-premise or cloud storage.
I encourage you to download and evaluate BDRSuite to experience firsthand the benefits we’ve mentioned. BDRSuite’s free version lets you back up to 10 virtual machines indefinitely, complete with all features and functionalities.
Wrap up
Abyss Locker is ransomware that targets VMware ESXi virtualization environments. More precisely, it targets virtual machines, encrypts them, and makes them unusable until the victim makes a payment in one of the cryptocurrencies, mostly Bitcoin.
It focuses on ESXi environments with weak SSH credentials, executing brute force attacks to gain access.
There are two ways you can protect against Abyss Locker. The first is to properly secure your ESXi environments. The hardening of any platform starts by keeping it up to date with the latest updates and security fixes. As this attack is related to weak SSH credentials, you need to harden SSH security.
The second way is to continuously backup your workload using BDRsuite. BDRsuite supports immutable backup, which helps you keep backups of your virtual machines unchanged.
This article provides a brief introduction to Abyss Locker and offers some tips on how to secure SSH.
Additionally, it highlights BDRsuite’s ransomware protection features.
Thank you for reading this article. I hope you found it valuable. After going through our blog, what kind of content are you most interested in exploring further? Feel free to share your thoughts and suggestions below.
Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.



Leave A Comment