As we look at the AZ-104 exam and prepare with a thorough understanding of the concepts, it is important to understand identity-based access for Azure Files. You can leverage Microsoft Entra ID (Azure Active Directory, a.k.a Azure AD) or even on-premises Active Directory Domain Services to safeguard data based on identity. Let’s consider AZ-104 identity-based access for Azure files and see how this can be implemented for storage file data.
What is Azure Files?
File servers that exist across many on-premises locations present challenges with file access for the hybrid workforce. With Azure files, you can migrate on-premises file resources to the cloud and access Azure file shares using Azure or AD DS authentication.
Azure Files supports server message block (SMB) services hosted in the Microsoft Azure cloud that allows hosting file shares in the cloud. It has integration with Microsoft Entra ID, which provides a cloud-based identity framework for authentication.
Organizations can also use their on-premises AD DS identity-based authentication.
This ensures all file shares are accessible only to authenticated users or groups and allows managing access control and granting file-level permissions.
Note the following Azure File share targets
- File share type Standard file shares (GPv2) – SMB, No NFS
- LRS/ZRS Standard file shares (GPv2) – SMB, No NFS
- GRS/GZRS Premium file shares (FileStorage), LRS/ZRS – SMB & NFS
The Role of Microsoft Entra in Securing Azure File Shares
With its advanced identity and access management capabilities, Microsoft Entra is the modern way for admins to secure Azure resources. It allows creating and managing identities, including service principals, which are crucial in automating access to Azure services.
Microsoft Entra ID ensures the identity is securely managed and authenticated and provides a layer of security essential for accessing Azure file shares.
Creating an Azure File Share
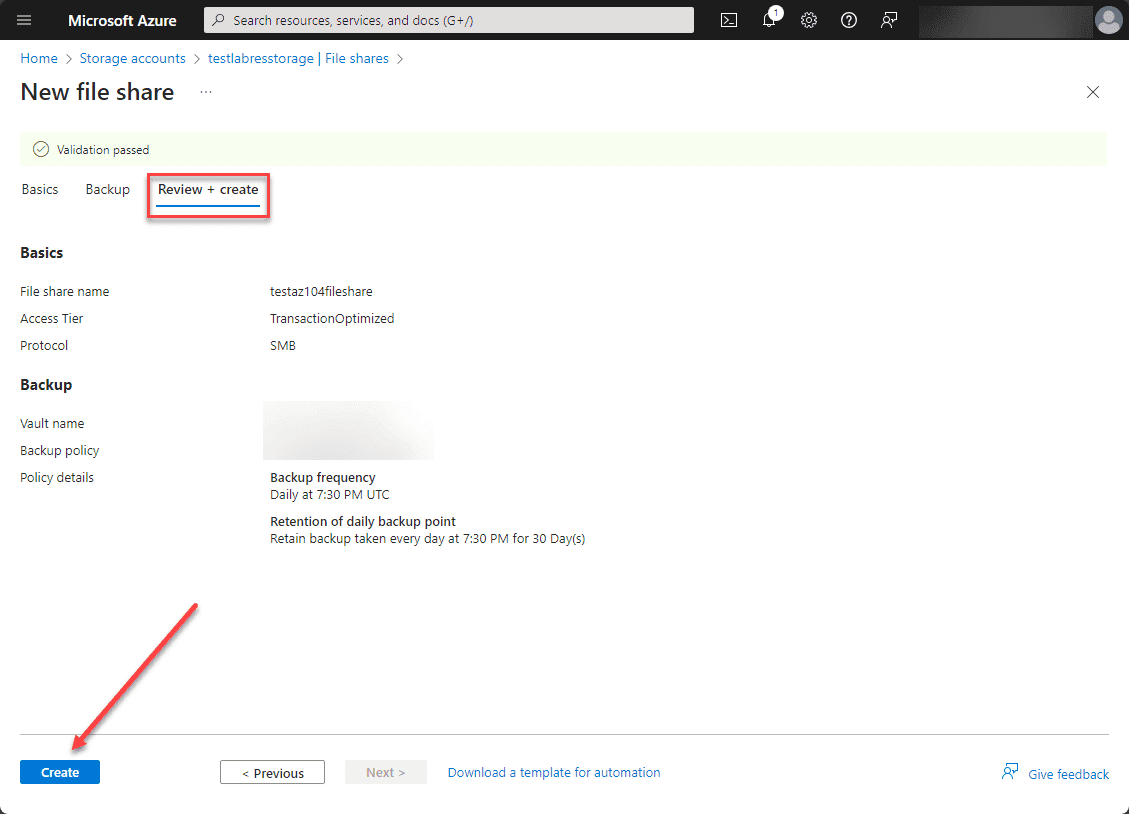
The process of creating an Azure File Share is straightforward. You must first have an Azure storage account. Once you have created a new Azure Storage account, you can then create a new Azure File Share.
When you are in the Storage Account blade, click the Data storage > File shares link in the Azure Portal.
Next, click the + File share.
It will launch the New file share wizard.
On the backup screen you can configure Azure backups to cover your file shares.
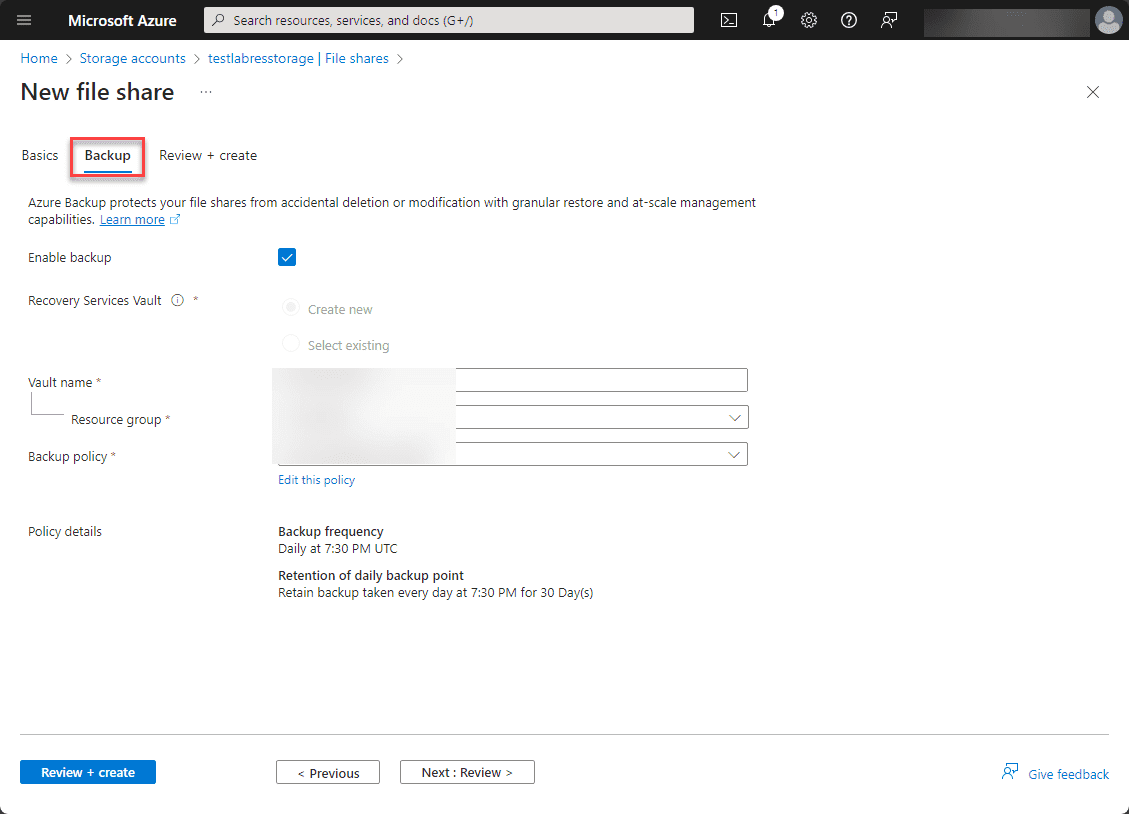
Finally, click the Create button to create the Azure file share.
Storage accounts and identity-based access Azure file shares
The foundation of Azure Files is the Azure storage account. This involves configuring storage accounts to use Azure AD for identity-based authentication, enabling Azure Role-Based Access Control (Azure RBAC) for granular access management, and applying Windows ACLs for file and directory-level permissions.
Manage access to Azure File Shares using identity-based authentication
In the File Shares blade, you have everything needed to manage access to the Azure file share. You can assign access rights using roles found in Microsoft Entra ID and other identity providers.
Enabling identity-based access
You can access your file share using your storage account key by default. However, Azure Files supports identity-based access for Azure file shares. The process is straightforward. Navigate to your storage account and then to File Shares.
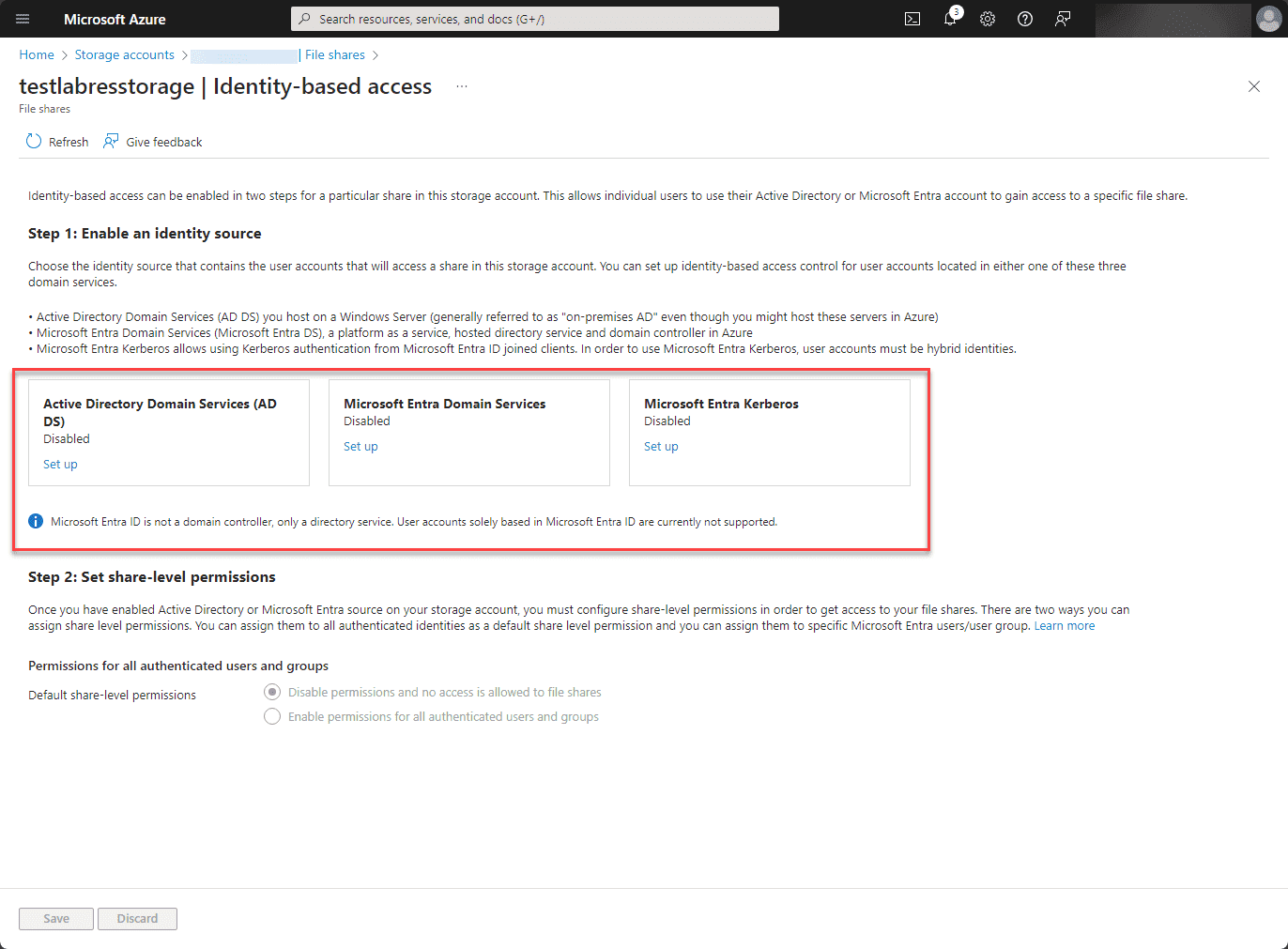
Once there, you will see the File share settings below. You will note that the identity-based access is not configured by default. So, we need to configure the identity source we want to use for authentication with Azure file shares.
Clicking the not configured link will allow you to configure identity-based access for the file shares in the storage account.
You will see the following three options to configure directory authentication separately:
- Active Directory Domain Services (AD DS) – This allows an Azure File Share to be domain-joined with on-premises Active Directory. There are five steps needed for this to work. You first domain-join the storage account with Active Directory. You use the join-az PowerShell cmdlet. Then, you create a shared ACL on the storage account, which will apply to all the shares underneath. Add a role assignment. Test your connection to the Azure File share. You can create a private endpoint if you can’t pass SMB traffic through the Internet, which most may have blocked
- Microsoft Entra Domain Services – This is formerly known as Azure Active Directory Domain Services, which grants access to the Azure file shares using Microsoft Entra ID
- Microsoft Entra Kerberos – Allows users to connect to Azure Files over the Internet without connectivity (line-of-sight) to domain controllers. User accounts using this method for authentication must be hybrid accounts
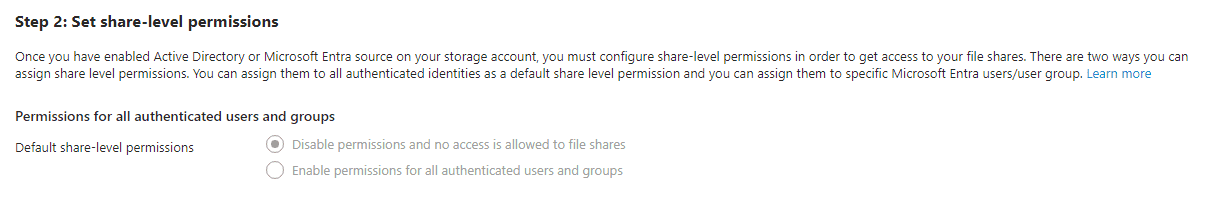
Follow the wizards for each identity solution to establish the configuration needed for the setup. After activating Active Directory or Microsoft Entra as a source for your storage account, it’s necessary to set up share-level permissions to access your file shares.
There are two methods for establishing these permissions. Firstly, you can allocate share-level permissions universally to all authenticated identities as a default setting. Secondly, you can assign permissions to particular Microsoft Entra users or user groups, tailoring access more specifically using built-in roles. You can also configure custom roles for access.
Wrapping up Azure Files with Microsoft Entra
Azure Files is a great solution that allows transcending beyond legacy Windows File Servers that exist on-premises and allows users to access files in the cloud using their current identity, whether Active Directory Domain Services or Microsoft Entra ID.
It provides scalability and accessibility, which is impossible with on-premises technologies, and allows organizations to grow and scale their file infrastructure as their needs change. For the AZ-104 exam, understand the concepts around Azure Files and identity-based authentication for directory and file access in Azure Files.
Read More:
Microsoft Azure Administrator: AZ-104: Azure Storage Access Keys – Part 25
Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.



Leave A Comment